ssh 的公钥和密钥_如何在Linux中创建和设置用于无密码和基于公钥的身份验证的SSH密钥?
ssh 的公钥和密钥
Ssh is a protocol designed to make network connections between hosts secure. Ssh is a defacto standard for Linux and related operating systems. Ssh encrypts the connection between sides. Ssh gives terminal access between host and server. To get a terminal there need to be an authentication process. The authentication process is generally password-based but there are some caveats for password-based authentication. Brute force attacks can guess the password and give access to the server. To make things more secure key-based authentication can be used. It is far more secure and practical to use in logins or batch operations.
Ssh是旨在使主机之间的网络连接安全的协议。 Ssh是Linux和相关操作系统的事实上的标准。 Ssh加密双方之间的连接。 Ssh提供主机和服务器之间的终端访问。 要获得终端,需要进行身份验证过程。 身份验证过程通常是基于密码的,但是对于基于密码的身份验证有一些警告。 蛮力攻击可以猜测密码并授予对服务器的访问权限。 为了使事情更加安全,可以使用基于密钥的身份验证。 在登录或批处理操作中使用它更加安全实用。
创建密钥对 (Creating Key Pairs)
We will create key pairs. We may ask yourself why pair. Isn’t 1 key enough? In Asymmetric cryptography key pairs where each if different is used to complete each other. One key is named public which is known by the public. One key is named private and only known by the owner.
我们将创建密钥对。 我们可能会问自己为什么配对。 1把钥匙还不够吗? 在非对称加密密钥对中,如果使用不同的密钥对,则它们将彼此完成。 一把钥匙叫做public,这是公众所知道的。 一把钥匙被称为私人钥匙,只有主人知道。
$ ssh-keygen -t rsa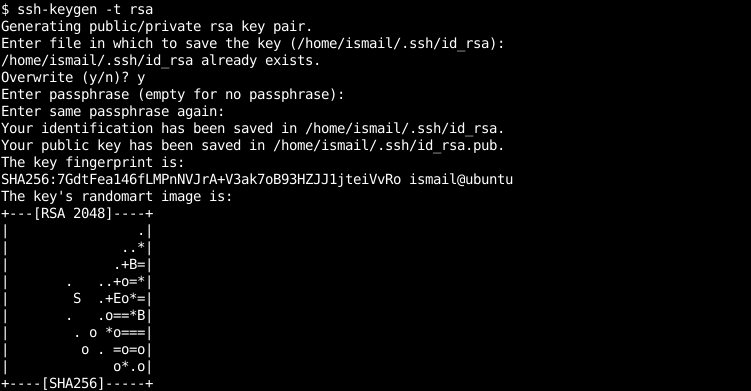
During the RSA public and private key generation, we will be asked some questions like below. We can answer them all skip all of them just with Enter key.
在生成RSA公钥和私钥的过程中,我们将被询问以下一些问题。 我们可以回答所有问题,仅需按Enter键即可跳过所有问题。
- “Enter file in which to save the key (/home/ismail/.ssh/id_rsa):” question is used to specify the RSA key pair which name is `id_rsa` by default and the path where the current user home path under the `.ssh` directory.“输入要在其中保存密钥的文件(/home/ismail/.ssh/id_rsa):”问题用于指定默认名称为“ id_rsa”的RSA密钥对以及该路径下当前用户主目录的路径。 .ssh目录。
- “Overwrite y/n ?” will be asked if there is already a key with the specified path and name and accept to overwrite. If we will not use the old RSA key we can overwrite with “y” answer.“覆盖y / n吗?” 将会询问是否已存在具有指定路径和名称的密钥,并接受覆盖。 如果我们不使用旧的RSA密钥,则可以用“ y”答案覆盖。
- “Enter passphrase (empty for no passphrase)” question is used to protect created public and private key with encryption where we have to specify a passphrase“输入密码短语(空无密码短语)”问题用于通过加密保护创建的公钥和私钥,我们必须指定密码短语
- “Enter passphrase” line is used to check previously entered passphrase to prevent mistakes“输入密码”行用于检查先前输入的密码,以防止错误
We have created a key pair based RSA algorithm. Our key pairs are 2048 bit. So it is more secure as long as the longer key size. We can protect our key pair with passphrase but it is not practical for most situations. Our key pair is located by default users’ home directories .ssh file. Keep in mind that while working with ssh configuration we need root privileges. The best way to get root privileges uses the following command.
我们创建了一个基于密钥对的RSA算法。 我们的密钥对为2048位。 因此,只要密钥大小更长,它就会更加安全。 我们可以使用密码来保护密钥对,但是在大多数情况下并不实用。 默认情况下,我们的密钥对位于用户的主目录.ssh文件中。 请记住,在使用ssh配置时,我们需要root特权。 获得root特权的*佳方法是使用以下命令。
$ sudo su将用户SSH密钥添加到远程服务器 (Adding User SSH Key to Remote Server)
Now we have a key to use. We will use ssh-copy-id command where we specify the user we want to copy the key and the server hostname or IP address. In this example, we will copy already created an SSH key for the user ismail in the 192.168.142.150.
现在我们有一个要使用的钥匙。 我们将使用ssh-copy-id命令,在其中指定要复制密钥的用户以及服务器主机名或IP地址。 在此示例中,我们将为用户ismail复制已创建的SSH密钥到192.168.142.150 。
$ ssh-copy-id[email protected]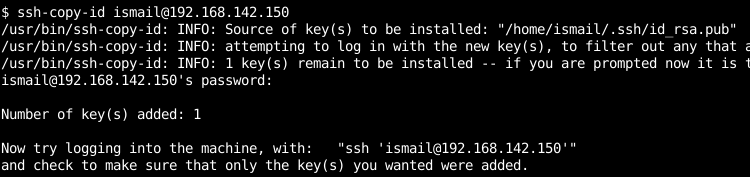
We can see that during the SSH key deployment some information is printed to the screen like source key which will be installed to the remote system. How many keys remained for installation? and at the end of the installation, the “Number of keys added” which is one in this case. Then the SSH command to login passwordless to the remote system with the specified user is printed where we can check like below.
我们可以看到,在SSH密钥部署期间,某些信息会像源密钥一样打印到屏幕上,该信息将被安装到远程系统上。 剩下多少个安装密钥? 在安装结束时,“已添加密钥数”在这种情况下为1。 然后,将打印SSH命令以使用指定的用户无密码地登录到远程系统,在此我们可以进行如下检查。
$ ssh[email protected]
禁用SSH配置的基于密码的身份验证(Disable Password-Based Authentication for SSH Configuration)
After completing these steps we can disable password-based authentication for ssh server.
完成这些步骤后,我们可以为ssh服务器禁用基于密码的身份验证。
$ vim /etc/ssh/sshd_configOpen sshd_config file and change PasswordAuthentication and PermitRootLogin line like below
打开sshd_config文件并更改PasswordAuthentication和PermitRootLogin行,如下所示
-
PasswordAuthentication no
-
PermitRootLogin without-password
应用SSH服务器配置 (Apply SSH Server Configuration)
Then restart SSH server to load with the new configuration.
然后重新启动SSH服务器以加载新配置。
$ sudo systemctl restart ssh检查SSH服务器状态 (Check SSH Server Status)
Check if the SSH is working with the systemctl command like below. We will see that the SSH is working properly in the Active line with a green color. If there is an error you can revert back to the original configuration and restart the SSH service again which is described previously.
检查SSH是否与systemctl命令一起使用,如下所示。 我们将看到SSH在绿色的Active行中正常运行。 如果出现错误,您可以恢复到原始配置,然后再次重新启动SSH服务,如前所述。
$ systemctl status ssh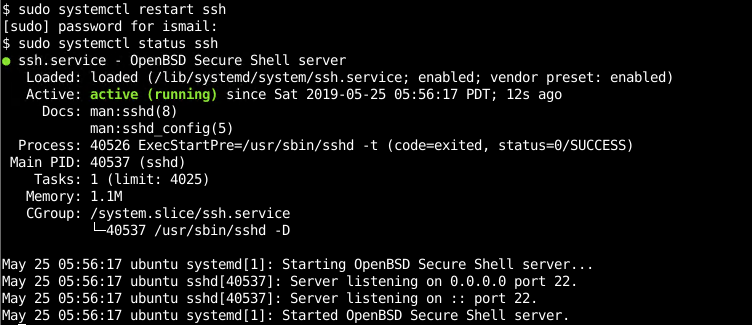
( )
如何在Linux中创建和设置用于无密码和基于公钥的身份验证的SSH密钥? 信息图 (How To Create and Setup SSH Keys For Passwordless and Public Key Based Authentication In Linux? Infographic)
